Microsoft Threat Protection ‘Jupyter notebook’
(EN)
L;DR — I’ve created a Microsoft Threat Protection advanced hunting Jupyter notebook and shared it on my GitHub repository: https://github.com/maartengoet/notebooks/blob/master/mtp_hunting.ipynb
Microsoft Threat Protection
Microsoft Threat Protection unifies pre- and post-breach enterprise defenses and natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
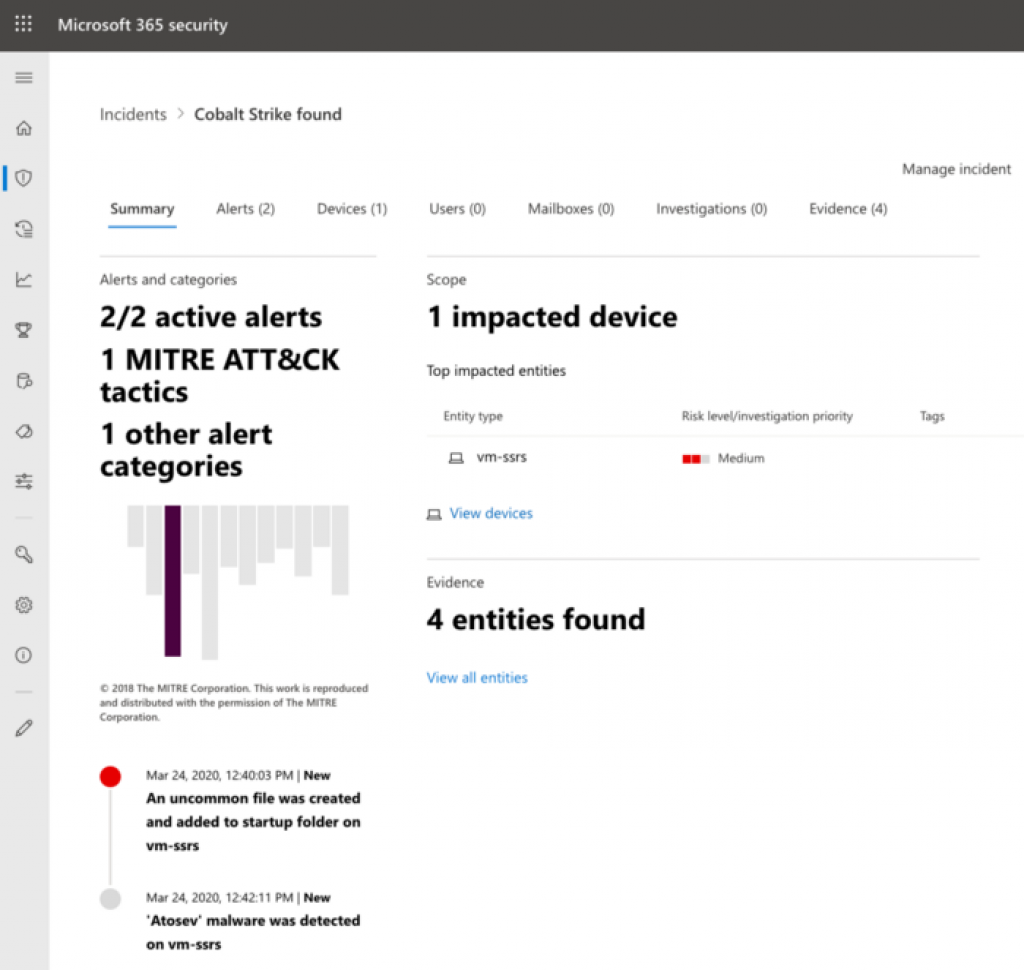
It combines the power of Microsoft Defender ATP, Azure AD Identity Protection, Microsoft Cloud App Security and Office 365 ATP. Do you have 2 or more of these products in your environment, then try out MTP by going to https://security.microsoft.com
Advanced Hunting
Microsoft Threat Protection features a built-in Advanced Hunting capability, much like the one in Microsoft Defender ATP.
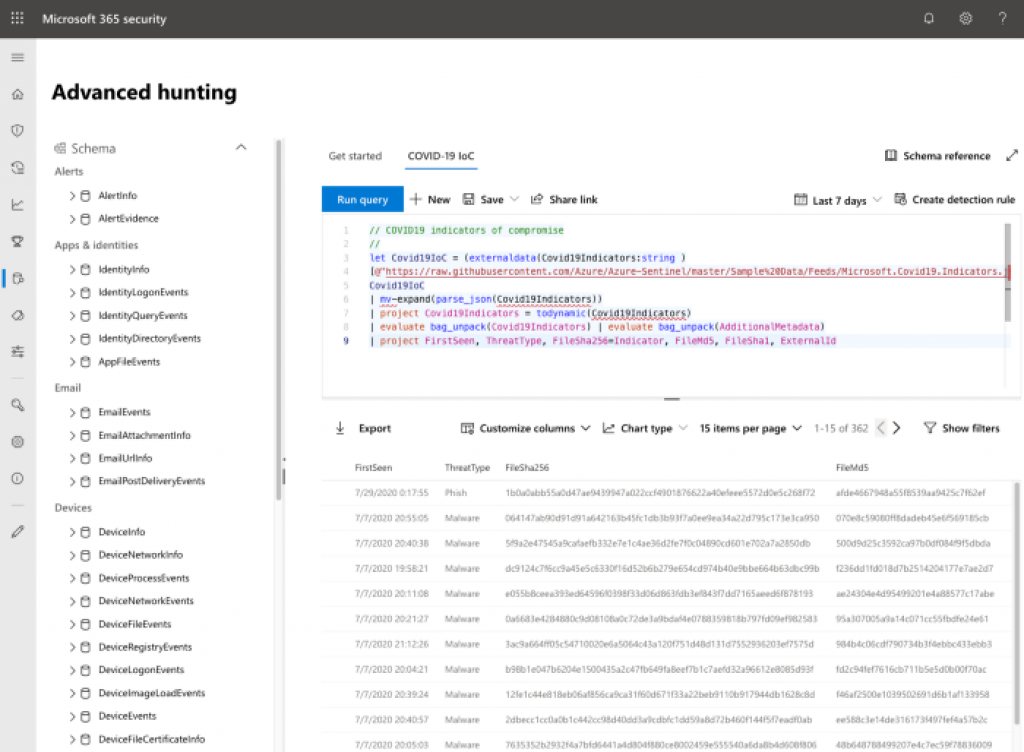
Are you new to advanced hunting? I’ve published a lengthy blog earlier that takes you down the Rabbit Hole and learns you the basics of analyzing malware, as discovered by Microsoft Threat Protection.
MTP Advanced Hunting blog here: https://medium.com/wortell/microsoft-threat-protection-going-down-the-rabbit-hole-6f917d7c98f
Jupyter
Although the built-in KQL-based Advanced Hunting possibilities already satisfy most incident investigations, a complex investigation could require that the hunting professionals starts using Jupyter.
Although more advanced, and certainly requires some more experiences (and preferably Python skills), it extends Microsoft Threat Protection in many ways. For instance, by combining note taking (markdown) with advanced code (python) and the ability to pull in 3rd party data sources.
PRO TIP: Ian Hellen (MS Threat Intelligence Center) and myself presented on Jupyter-based hunting and the MSTIC toolkit at MS Ignite 2019.
Recording here: https://myignite.techcommunity.microsoft.com/sessions/83948?source=sessions
Managed eXtended Detection and Response
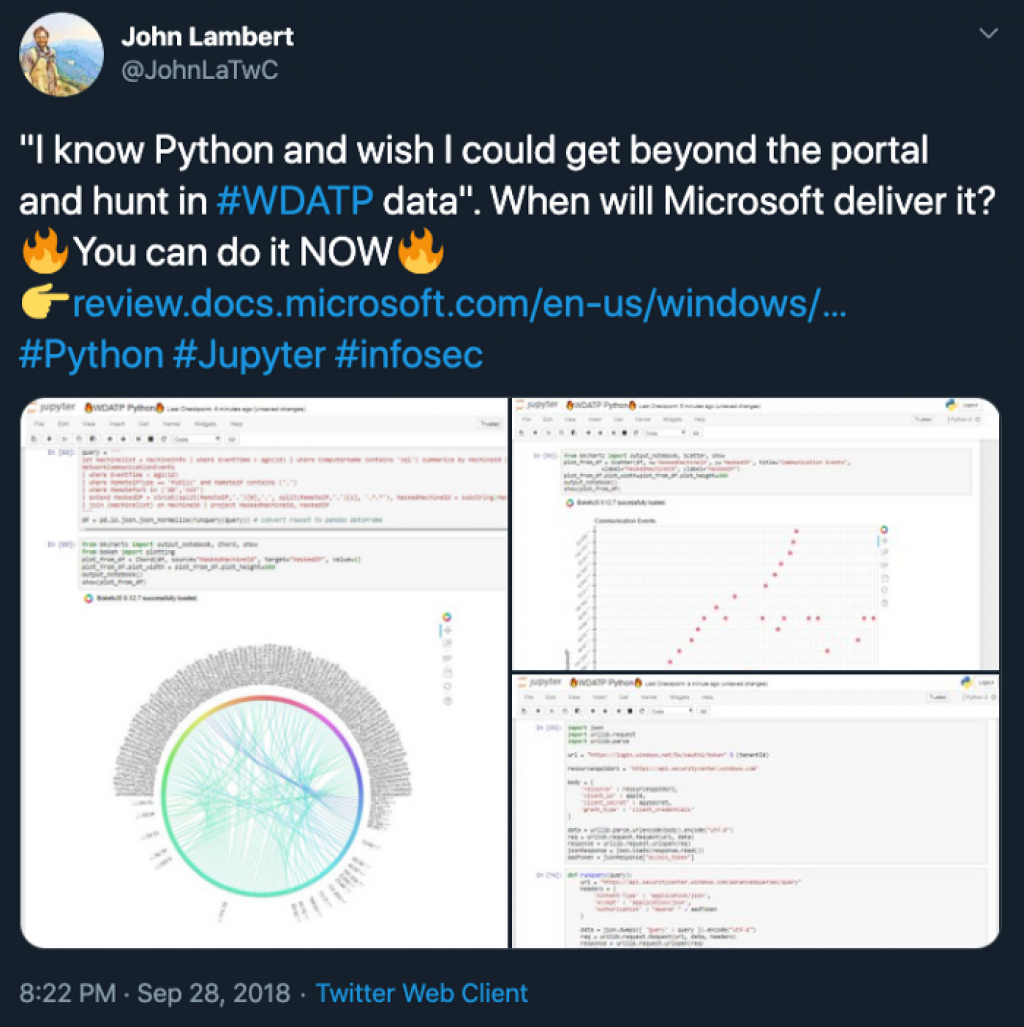
I’ve written an introduction into Jupyter and hunting in an earlier blog. Have a look at that article if you need more information on this.
Hunting with Jupyter blog here: https://medium.com/@maarten.goet/threat-hunting-in-the-cloud-with-azure-notebooks-supercharge-your-hunting-skills-using-jupyter-8d69218e7ca0
Visual Studio Code
You might think that using Jupyter will be hard, but that is not the case. Better yet: you can use the IDE you already know and love — Visual Studio Code. Microsoft’s Python extension includes support for Jupyter.
Visual Studio Code + Jupyter blog here: https://medium.com/@maarten.goet/visual-studio-code-the-swiss-army-knife-for-threat-hunting-with-azure-sentinel-503e7ef38c96
Prepare
Before we can use the Microsoft Threat Protection API from a Jupyter notebook, we first have to create an Application + Secret pair in Azure Active Directory. Use the Microsoft Threat Protection API, select Application Permissions and select the AdvancedHunting.Read.All
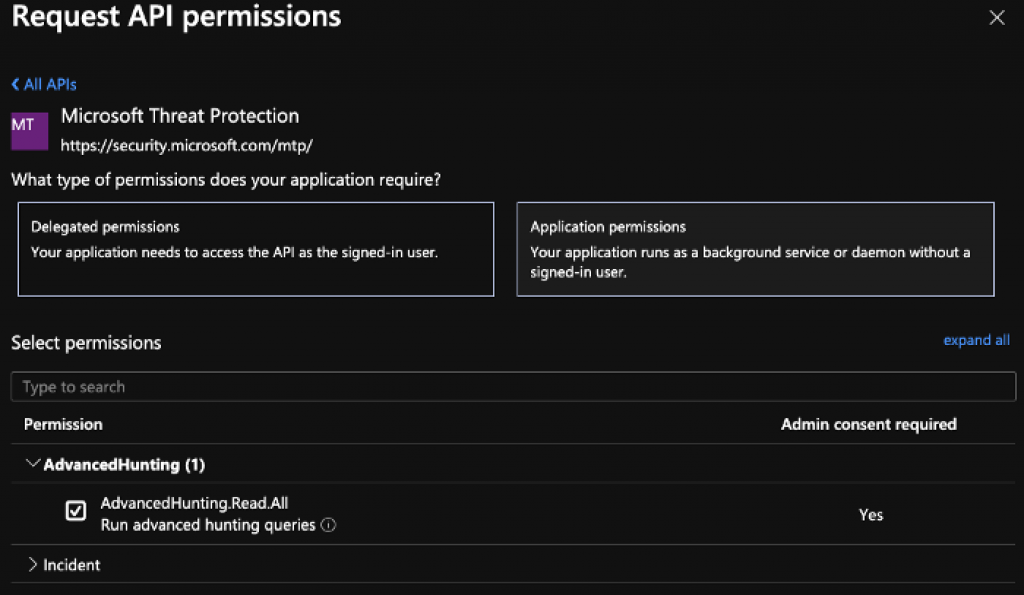
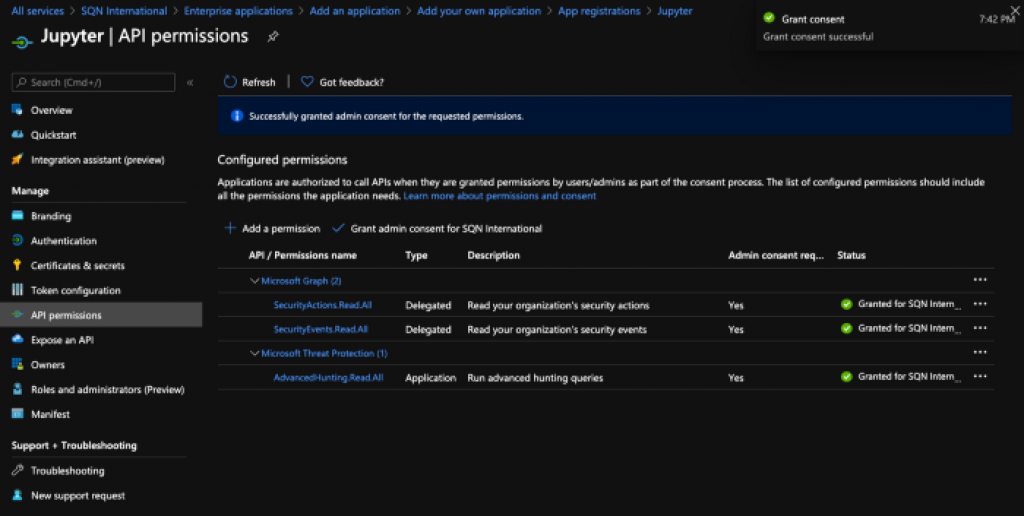
PRO TIP: Did you already create an Azure AD Application for hunting with Microsoft Defender ATP? Make sure you add the new / extra permissions for the MTP API!
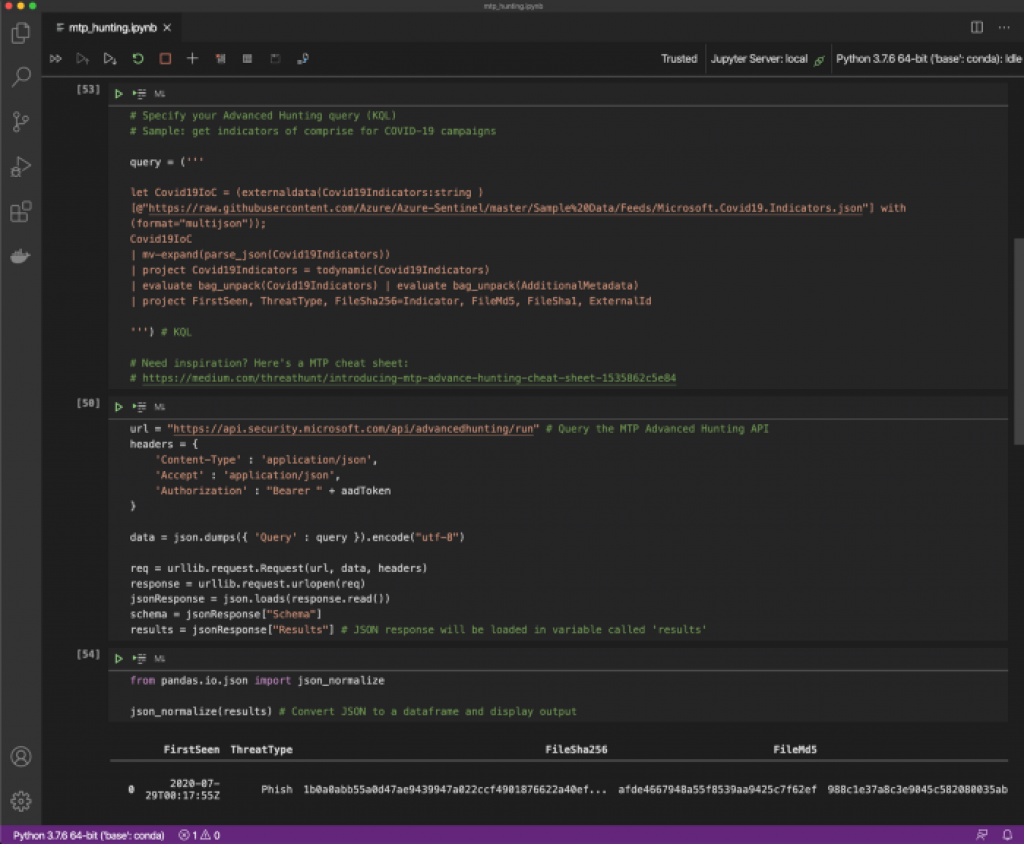
Advanced Hunting notebook
I’ve not seen a sample Advanced Hunting notebook for Microsoft Threat Protection from the community yet, so I figured I would create one and contribute back.
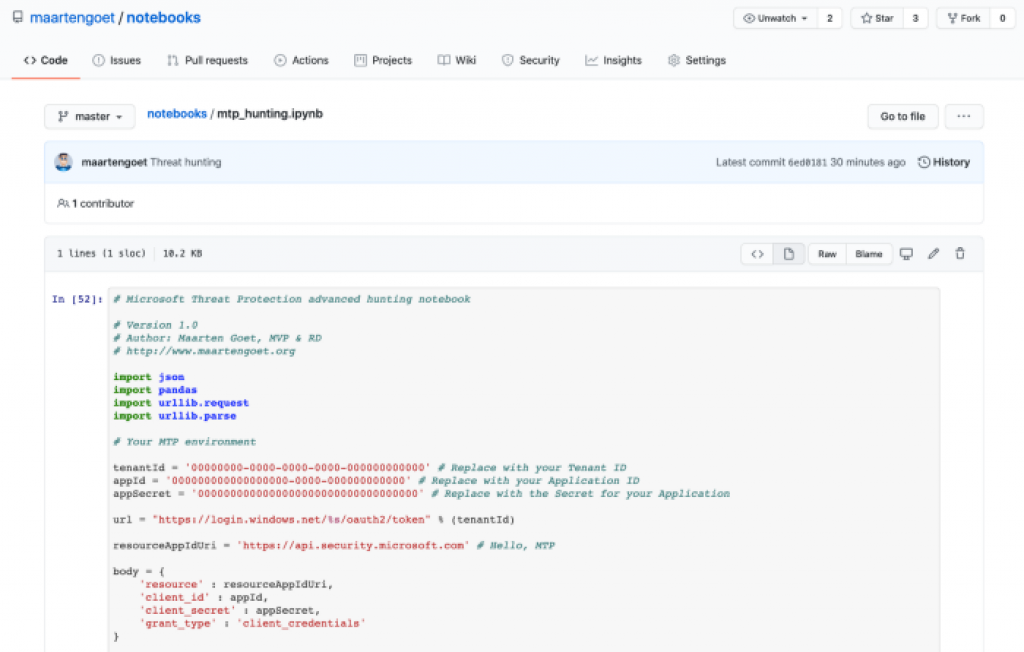
Download the MTP Advanced Hunting notebook here:
https://github.com/maartengoet/notebooks/blob/master/mtp_hunting.ipynb
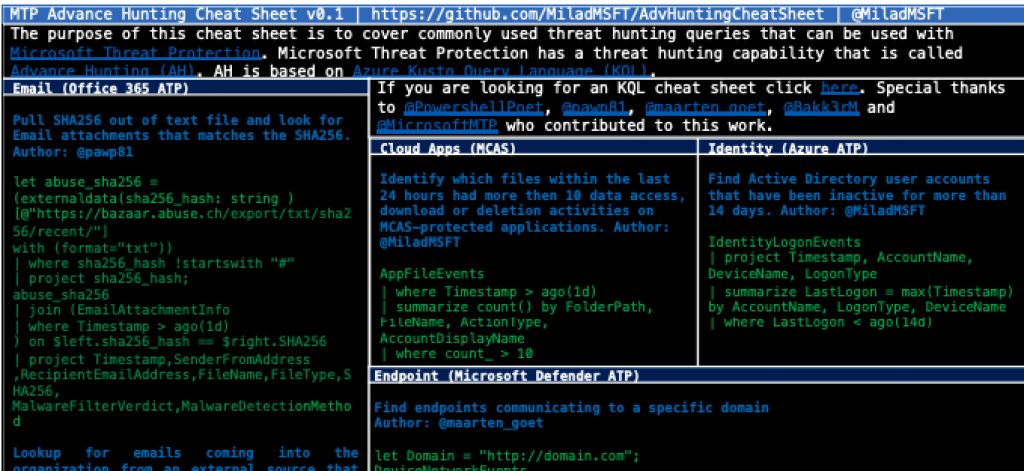
MTP Cheat Sheet
In search of some good MTP Advanced Hunting query samples? Milad Aslaner has you covered with his MTP Cheat Sheet!
MTP Advanced Hunting query cheat sheet here: https://medium.com/threathunt/introducing-mtp-advance-hunting-cheat-sheet-1535862c5e84
Happy hunting!